
Before you begin
- Labs create a Google Cloud project and resources for a fixed time
- Labs have a time limit and no pause feature. If you end the lab, you'll have to restart from the beginning.
- On the top left of your screen, click Start lab to begin
Configure the Firewall
/ 30
Launch client VMs
/ 30
Launch Server VMs
/ 20
Create the Private Zone
/ 20
Cloud DNS routing policies enable users to configure DNS based traffic steering. A user can either create a Weighted Round Robin (WRR) routing policy or a Geolocation (GEO) routing policy. You can configure routing policies by creating special ResourceRecordSets with special routing policy values.
Use WRR to specify different weights per ResourceRecordSet for the resolution of domain names. Cloud DNS routing policies help ensure that traffic is distributed across multiple IP addresses by resolving DNS requests according to the configured weights.
In this lab, you will configure and test the Geolocation routing policy. Use GEO to specify source geolocations and to provide DNS answers corresponding to those geographies. The geolocation routing policy applies the nearest match for the source location when the traffic source location doesn't match any policy items exactly.
You will learn how to:
example.com
Use the default VPC network to create all the virtual machines (VM) and launch client VMs in 3 Google Cloud locations: one in the United States, another in Europe, and another in Asia. To demonstrate the Geolocation routing policy behavior, you will create the server VMs only in two of those location - in the United States and in Europe. The archirtecture will look similar to what is shown in the graphic. (Note that the actual regions and zones within the United States and Europe may differ from those shown in the graphic.)
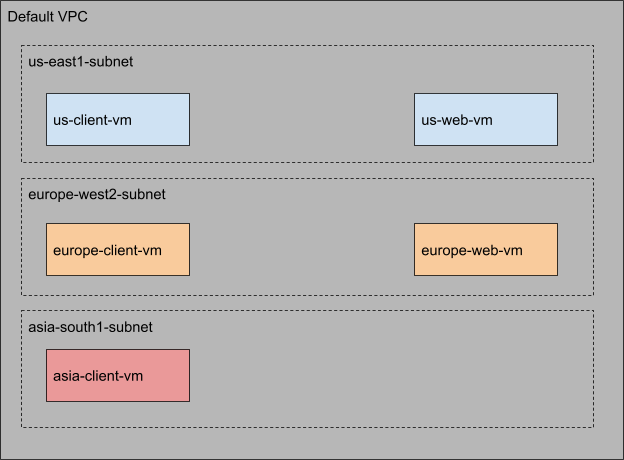
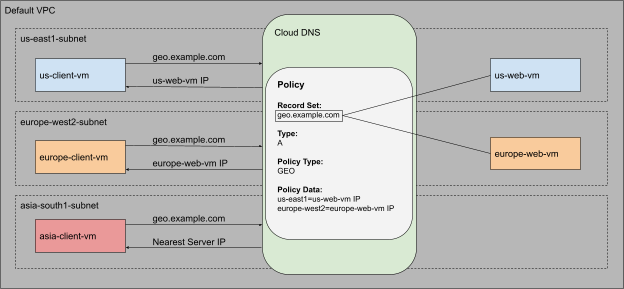
You will use Cloud DNS routing policies and create ResourceRecordSets for geo.example.com and configure the Geolocation policy to help ensure that a client request is routed to a server in the client's closest region.
This Qwiklabs hands-on lab lets you do the lab activities yourself in a real cloud environment, not in a simulation or demo environment. It does so by giving you new, temporary credentials that you use to sign in and access Google Cloud for the duration of the lab.
To complete this lab, you need:
Click the Start Lab button. If you need to pay for the lab, a pop-up opens for you to select your payment method. On the left is a panel populated with the temporary credentials that you must use for this lab.
Copy the username, and then click Open Google Console. The lab spins up resources, and then opens another tab that shows the Choose an account page.
On the Choose an account page, click Use Another Account. The Sign in page opens.
Paste the username that you copied from the Connection Details panel. Then copy and paste the password.
After a few moments, the Cloud console opens in this tab.
Google Cloud Shell is a virtual machine that is loaded with development tools. It offers a persistent 5GB home directory and runs on the Google Cloud.
Google Cloud Shell provides command-line access to your Google Cloud resources.
In Cloud console, on the top right toolbar, click the Open Cloud Shell button.
Click Continue.
It takes a few moments to provision and connect to the environment. When you are connected, you are already authenticated, and the project is set to your PROJECT_ID. For example:
gcloud is the command-line tool for Google Cloud. It comes pre-installed on Cloud Shell and supports tab-completion.
Output:
Example output:
Output:
Example output:
Ensure that the Compute and the Cloud DNS APIs are enabled. In this section, you will enable the APIs manually, using gcloud commands.
gcloud services enable command to enable the Compute Engine API:This command can take a few minutes to complete.
gcloud services enable command to enable the Cloud DNS API:This command can take a few minutes to complete.
gcloud services list command to list all the enabled APIs. We should see compute.googleapis.com and dns.googleapis.com in the listed output.Output:
Before you create the client VMs and the web servers, you need to create two firewall rules.
firewall-rules create command can take a few minutes to complete. Please wait for the "Creating firewall...done" message before proceeding to the next step.Output:
Output:
Click Check my progress to verify the objective.
Now that the APIs are enabled, and the firewall rules are in place, the next step is to set up the environment. In this section, you will create 3 client VMs, one in each region.
gcloud compute instances create command to create the client VMs:This command can take a few minutes to complete. Please wait for a "Created" message before moving to the next step. Note that you may see a different zone in gcloud than in the sample output shown below.
Output:
Note that you may see a different zone in gcloud than in the sample output shown below.
Output:
Note that you may see a different zone in gcloud than in the sample output shown below.
Output:
Click Check my progress to verify the objective.
Now that the client VM's are up and running, the next step is to create the server VMs. You will use a startup script to configure and set up the web servers. As mentioned earlier, you will create the server VMs only in 2 regions: us-east1 and europe-west2.
gcloud compute instances create command to create the server VMs. The compute instance create command can take a few minutes to complete. Please wait for a "Created" message before moving to the next step.Note that you may see a different zone in gcloud than in the sample output shown below.
Output:
Note that you may see a different zone in gcloud than in the sample output shown below.
Output:
Click Check my progress to verify the objective.
Before you configure Cloud DNS, note the Internal IP addresses of the web servers. You need these IPs to create the routing policy. In this section, you will use the gcloud compute instances describe command to save the internal IP addresses as environment variables.
Now that your client and server VMs are running, it's time to configure the DNS settings. Before creating the A records for the web servers, you need to create the Cloud DNS Private Zone.
For this lab, use the example.com domain name for the Cloud DNS zone.
gcloud dns managed-zones create command to create the zone:Output:
In this section, configure the Cloud DNS Geolocation Routing Policy. You will create a record set in the example.com zone that you created in the previous section.
gcloud dns record-sets create command to create the geo.example.com recordset:You are creating an A record with a Time to Live (TTL) of 5 seconds. The policy type is GEO, and the routing_policy_data field accepts a semicolon-delimited list of the format ${region}:${rrdata},${rrdata}.
Output:
dns record-sets list command to verify that the geo.example.com DNS record is configured as expected:The output shows that an A record with a TTL of 5 is created for geo.example.com, and the data matches our server set up in each region.
Note that in gcloud, the DATA value under geo.example.com may include United States and Europe regions that differ from the sample output below.
Output:
Click Check my progress to verify the objective.
It's time to test the configuration. In this section, you will SSH into all the client VMs. Since all of the web server VMs are behind the geo.example.com domain, you will use CURL command to access this endpoint.
Since you are using a Geolocation policy, the expected result is that:
gcloud compute ssh command to log into the client VM:Once complete, the command line should change to "user_name@europe-client-vm:~$"
Output:
curl to access the web serverCURL command to access the geo.example.com endpoint. The loop is configured to run the command ten times with a sleep timer of 6 seconds:Since the TTL on the DNS record is set to 5 seconds, a sleep timer of 6 seconds has been added. The sleep timer will make sure that you get an uncached DNS response for each cURL request. This command will take approximately one minute to complete.
The expected output is "Page served from:
exit" in the VM's command prompt. This will bring you back to the Cloud Shell console.Now perform the same test from the client VM in the US.
gcloud command below to SSH into the us-client-vm:curl command to access geo.example.com:Now analyze the output to see which server is responding to the request. The client should always receive a response from a server in the client's region. The expected output is "Page served from:
Once you have run the test multiple times, exit the client VM in the US by typing "exit" in the VM's command prompt.
So far you have tested the setup from the United States and Europe. You have servers running in both the regions and have matching record sets for both the regions in Cloud DNS routing policy. There is no matching policy item for the region within Asia (selected earlier) in the Cloud DNS routing policy.
The Geolocation policy will apply a "nearest" match for source location when the source of the traffic doesn't match any policy items exactly. This means that the Asia client should be directed to the nearest web server.
In this section, you will resolve the geo.example.com domain from the client VM in Asia and will analyze the response.
<SELECTED-ZONE>, use the zone that you used to create the Asia client.Analyze the output to see which server is responding to the request. Since there is no policy item for any of the Asia regions, Cloud DNS will direct the client to the nearest server.
Once you have run the test multiple times, exit the client VM in Asia by typing "exit" in the VM's command prompt.
Although all resources you used in this lab will be deleted when you finish, it is good practice to remove resources you no longer need to avoid unnecessary charges.
gcloud commands will delete all the resources that were created in the lab. (Note that SELECTED-ZONE is the Asia zone that you wrote down earlier.)In this lab, you configured and used Cloud DNS routing policies with Geolocation routing policy. You also verified the configuration and behavior of the Cloud DNS routing policy by observing the HTTP response when accessing the web servers.
You can read more about Cloud DNS routing policies.
When you have completed your lab, click End Lab. Google Cloud Skills Boost removes the resources you’ve used and cleans the account for you.
You will be given an opportunity to rate the lab experience. Select the applicable number of stars, type a comment, and then click Submit.
The number of stars indicates the following:
You can close the dialog box if you don't want to provide feedback.
For feedback, suggestions, or corrections, please use the Support tab.
Copyright 2022 Google LLC All rights reserved. Google and the Google logo are trademarks of Google LLC. All other company and product names may be trademarks of the respective companies with which they are associated.


此内容目前不可用
一旦可用,我们会通过电子邮件告知您

太好了!
一旦可用,我们会通过电子邮件告知您


One lab at a time
Confirm to end all existing labs and start this one
