Checkpoints
Create Cloud SQL instance using Terraform script
/ 100
Cloud SQL with Terraform
GSP234
Overview
In this hands-on lab you will learn how to create Cloud SQL instances with Terraform, then set up the Cloud SQL Proxy, testing the connection with a MySQL client.
Objectives
In this lab, you will:
- Create a Cloud SQL instance
- Install the Cloud SQL Proxy
- Test connectivity with MySQL client using Cloud Shell
Setup
Before you click the Start Lab button
Read these instructions. Labs are timed and you cannot pause them. The timer, which starts when you click Start Lab, shows how long Google Cloud resources will be made available to you.
This hands-on lab lets you do the lab activities yourself in a real cloud environment, not in a simulation or demo environment. It does so by giving you new, temporary credentials that you use to sign in and access Google Cloud for the duration of the lab.
To complete this lab, you need:
- Access to a standard internet browser (Chrome browser recommended).
- Time to complete the lab---remember, once you start, you cannot pause a lab.
How to start your lab and sign in to the Google Cloud console
-
Click the Start Lab button. If you need to pay for the lab, a pop-up opens for you to select your payment method. On the left is the Lab Details panel with the following:
- The Open Google Cloud console button
- Time remaining
- The temporary credentials that you must use for this lab
- Other information, if needed, to step through this lab
-
Click Open Google Cloud console (or right-click and select Open Link in Incognito Window if you are running the Chrome browser).
The lab spins up resources, and then opens another tab that shows the Sign in page.
Tip: Arrange the tabs in separate windows, side-by-side.
Note: If you see the Choose an account dialog, click Use Another Account. -
If necessary, copy the Username below and paste it into the Sign in dialog.
{{{user_0.username | "Username"}}} You can also find the Username in the Lab Details panel.
-
Click Next.
-
Copy the Password below and paste it into the Welcome dialog.
{{{user_0.password | "Password"}}} You can also find the Password in the Lab Details panel.
-
Click Next.
Important: You must use the credentials the lab provides you. Do not use your Google Cloud account credentials. Note: Using your own Google Cloud account for this lab may incur extra charges. -
Click through the subsequent pages:
- Accept the terms and conditions.
- Do not add recovery options or two-factor authentication (because this is a temporary account).
- Do not sign up for free trials.
After a few moments, the Google Cloud console opens in this tab.

Activate Cloud Shell
Cloud Shell is a virtual machine that is loaded with development tools. It offers a persistent 5GB home directory and runs on the Google Cloud. Cloud Shell provides command-line access to your Google Cloud resources.
- Click Activate Cloud Shell
at the top of the Google Cloud console.
When you are connected, you are already authenticated, and the project is set to your Project_ID,
gcloud is the command-line tool for Google Cloud. It comes pre-installed on Cloud Shell and supports tab-completion.
- (Optional) You can list the active account name with this command:
- Click Authorize.
Output:
- (Optional) You can list the project ID with this command:
Output:
gcloud, in Google Cloud, refer to the gcloud CLI overview guide.
Cloud SQL
Cloud SQL is a fully managed database service that makes it easy to set up, maintain, manage, and administer your relational databases on Google Cloud. You can use Cloud SQL with either MySQL or PostgreSQL.
Task 1. Download necessary files
- Create a directory and fetch the required Terraform scripts from the Cloud Storage bucket with:
- Unzip the downloaded content:
Task 2. Understand the code
- Take a look at the contents of the
main.tffile:
Example output:
Next, you will update the variables.tf file to use the project ID and region allocatedß to this lab.
- Click on Open Editor in Cloud Shell.
- Open
variables.tfand modify theprojectandregionvariables to the values shown below:
- project:
- region:
When finished save the changes made.
Task 3. Run Terraform
The terraform init command is used to initialize a working directory containing Terraform configuration files.
This command performs several different initialization steps in order to prepare a working directory for use. This command is always safe to run multiple times, to bring the working directory up to date with changes in the configuration.
- Run
terraform init:
The terraform plan command is an optional but recommended command and is used to create an execution plan. Terraform performs a refresh, unless explicitly disabled, and then determines what actions are necessary to achieve the desired state specified in the configuration files.
This command is a convenient way to check whether the execution plan for a set of changes matches your expectations without making any changes to real resources or to the state. For example, terraform plan might be run before committing a change to version control, to create confidence that it will behave as expected.
- Run
terraform plan:
The optional -out argument can be used to save the generated plan to a file for later execution with terraform apply.
The terraform apply command is used to apply the changes required to reach the desired state of the configuration or the pre-determined set of actions generated by a terraform plan execution plan.
- Apply the Terraform plan you just created:
This will take a little while to complete. Once complete you will see an output as below:
Test completed task
Click Check my progress to verify your performed task.
Task 4. Cloud SQL Proxy
What the proxy provides
The Cloud SQL Proxy provides secure access to your Cloud SQL Second Generation instances without having to allowlist IP addresses or configure SSL.
Accessing your Cloud SQL instance using the Cloud SQL Proxy offers these advantages:
- Secure connections: The proxy automatically encrypts traffic to and from the database using TLS 1.2 with a 128-bit AES cipher; SSL certificates are used to verify client and server identities.
- Easier connection management: The proxy handles authentication with Cloud SQL, removing the need to provide static IP addresses.
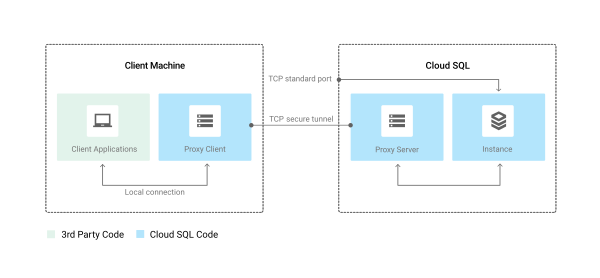
How the Cloud SQL Proxy works
The Cloud SQL Proxy works by having a local client, called the proxy, running in the local environment. Your application communicates with the proxy with the standard protocol used by your database. The proxy uses a secure tunnel to communicate with its companion process running on the server.
The following diagram shows how the proxy connects to Cloud SQL:
Task 5. Installing the Cloud SQL Proxy
- Download the proxy:
- Make the proxy executable:
You can install the proxy anywhere in your environment. The location of the proxy binaries does not impact where it listens for data from your application.
Proxy startup options
When you start the proxy, you provide it with the following sets of information:
- What Cloud SQL instances it should establish connections to
- Where it will listen for data coming from your application to be sent to Cloud SQL
- Where it will find the credentials it will use to authenticate your application to Cloud SQL
The proxy startup options you provide determine whether it will listen on a TCP port or on a Unix socket. If it is listening on a Unix socket, it creates the socket at the location you choose; usually, the /cloudsql/ directory. For TCP, the proxy listens on localhost by default.
Task 6. Test connection to the database
- Start by running the Cloud SQL proxy for the Cloud SQL instance:
- Run the following command:
Now you'll start another Cloud Shell tab by clicking on plus (+) icon. You'll use this shell to connect to the Cloud SQL proxy.
- Navigate to
sql-with-terraformdirectory:
- Get the generated password for MYSQL:
- Test the MySQL connection:
-
When prompted, enter the value of
MYSQL_PASSWORD, found in the output above, and press Enter. -
You should successfully log into the MYSQL command line. Exit from MYSQL by typing Ctrl + D.
If you go back to the first Cloud Shell tab you'll see logs for the connections made to the Cloud SQL Proxy.
Task 7. Test your understanding
Below are multiple-choice questions to reinforce your understanding of this lab's concepts. Answer them to the best of your abilities.
Congratulations!
In this lab, you used Terraform to create a Cloud SQL instance and set up the Cloud SQL Proxy. You then tested the connection between the two with a MySQL client.
Finish your quest
This self-paced lab is part of the Managing Cloud Infrastructure with Terraform and Cloud SQL quests. A quest is a series of related labs that form a learning path. Completing a quest earns you a badge to recognize your achievement. You can make your badge or badges public and link to them in your online resume or social media account. Enroll in Managing Cloud Infrastructure with Terraform or Cloud SQL and get immediate completion credit. See the Google Cloud Skills Boost catalog to see all available quests.
Take your next lab
Continue your learning with Using a NAT Gateway with Kubernetes Engine, or check out these suggestions:
Next steps / learn more
Read about how to manage Google Cloud projects with Terraform
Google Cloud training and certification
...helps you make the most of Google Cloud technologies. Our classes include technical skills and best practices to help you get up to speed quickly and continue your learning journey. We offer fundamental to advanced level training, with on-demand, live, and virtual options to suit your busy schedule. Certifications help you validate and prove your skill and expertise in Google Cloud technologies.
Manual Last Updated October 26, 2023
Lab Last Tested October 30, 2023
Copyright 2024 Google LLC All rights reserved. Google and the Google logo are trademarks of Google LLC. All other company and product names may be trademarks of the respective companies with which they are associated.