
Before you begin
- Labs create a Google Cloud project and resources for a fixed time
- Labs have a time limit and no pause feature. If you end the lab, you'll have to restart from the beginning.
- On the top left of your screen, click Start lab to begin
This lab was developed with our partner, Palo Alto Networks. Your personal information may be shared with Palo Alto Networks, the lab sponsor, if you have opted in to receive product updates, announcements, and offers in your Account Profile.
In this lab, use Cortex XSOAR (XSOAR) to automate incident response to phishing attacks.
The lab uses a real spear phishing attack against a fictional bank, Galactic Ministry of Finance, by infiltrating the bank's e-mail server. After infiltration, the attacker sends phishing e-mails to executives at a partnering bank, Bordeaux Bank, during peak business hours.
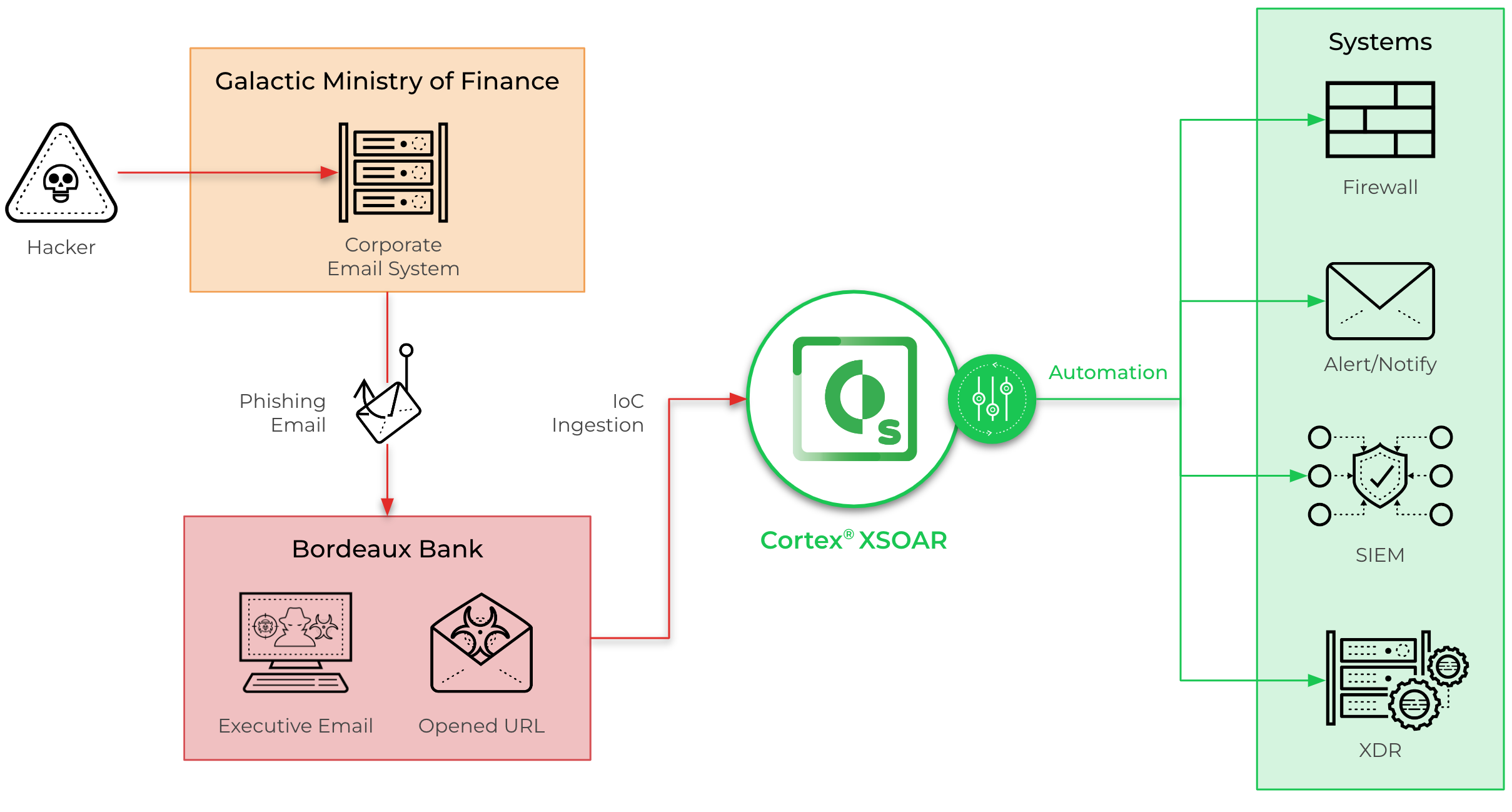
In this lab, you will perform the following tasks:
Read these instructions. Labs are timed and you cannot pause them. The timer, which starts when you click Start Lab, shows how long Google Cloud resources are made available to you.
This hands-on lab lets you do the lab activities in a real cloud environment, not in a simulation or demo environment. It does so by giving you new, temporary credentials you use to sign in and access Google Cloud for the duration of the lab.
To complete this lab, you need:
Click the Start Lab button. If you need to pay for the lab, a dialog opens for you to select your payment method. On the left is the Lab Details pane with the following:
Click Open Google Cloud console (or right-click and select Open Link in Incognito Window if you are running the Chrome browser).
The lab spins up resources, and then opens another tab that shows the Sign in page.
Tip: Arrange the tabs in separate windows, side-by-side.
If necessary, copy the Username below and paste it into the Sign in dialog.
You can also find the Username in the Lab Details pane.
Click Next.
Copy the Password below and paste it into the Welcome dialog.
You can also find the Password in the Lab Details pane.
Click Next.
Click through the subsequent pages:
After a few moments, the Google Cloud console opens in this tab.

In this task, take a moment to review the limitations of current solutions in effectively addressing phishing attacks.
What is phishing?
What are some current limitations with today's systems in addressing phishing emails?
How does Cortex XSOAR address these limitations?
In this task, learn about incidents within the Cortex XSOAR platform. An incident refers to a security event or breach that requires investigation, analysis, and remediation. When an incident occurs, XSOAR provides a centralized platform for managing and coordinating the response efforts.
In this step, create an incident for the phishing attack. Creating incidents allows you to choose a scenario that best fits your specific use-case.
Access Cortex XSOAR using the URL and credentials below.
| Key | Value |
|---|---|
| Console | |
| Username | |
| Password |
Go to Incidents. Set the Created range to All times.
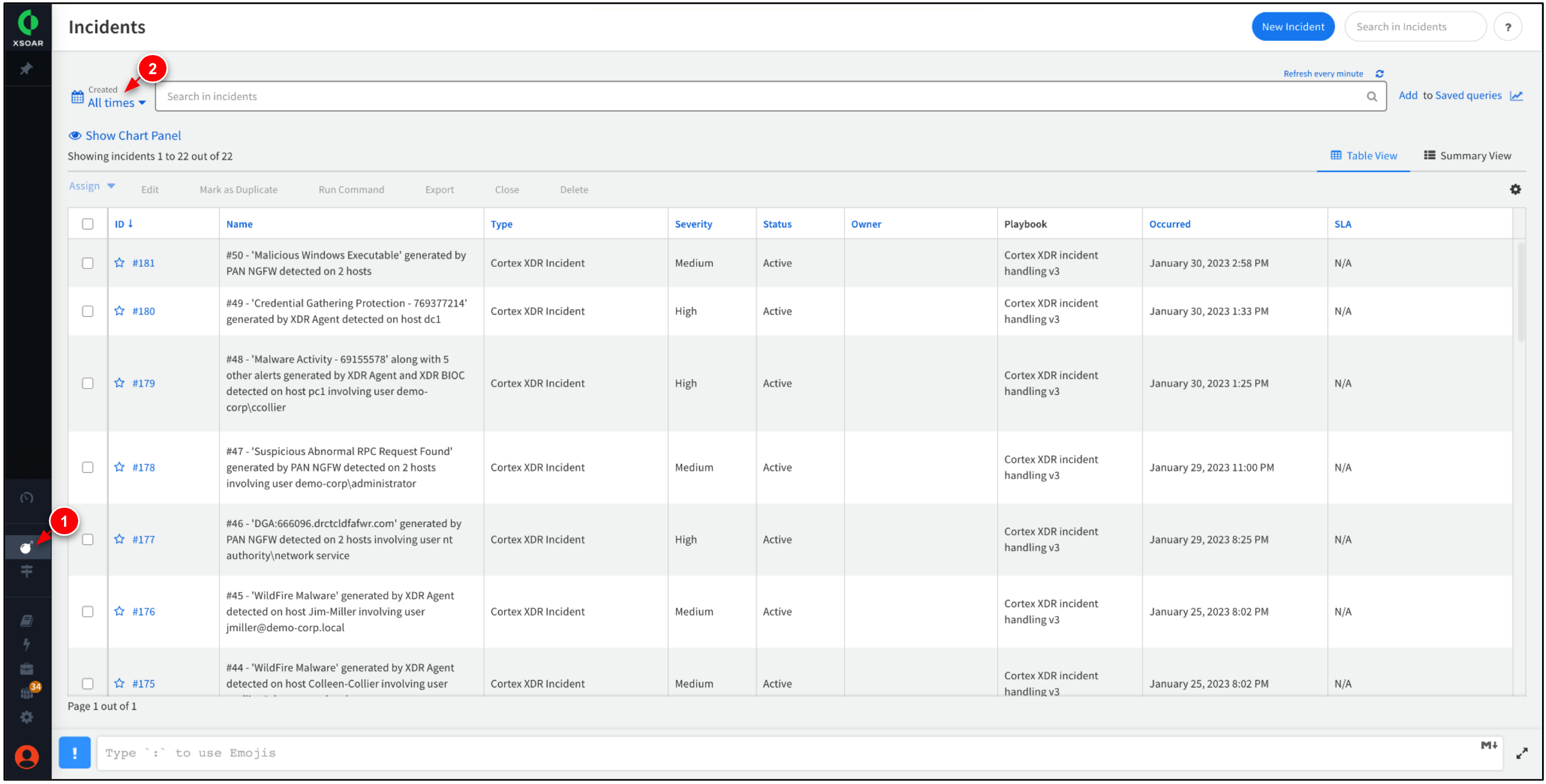
Click New Incident to create a new incident.
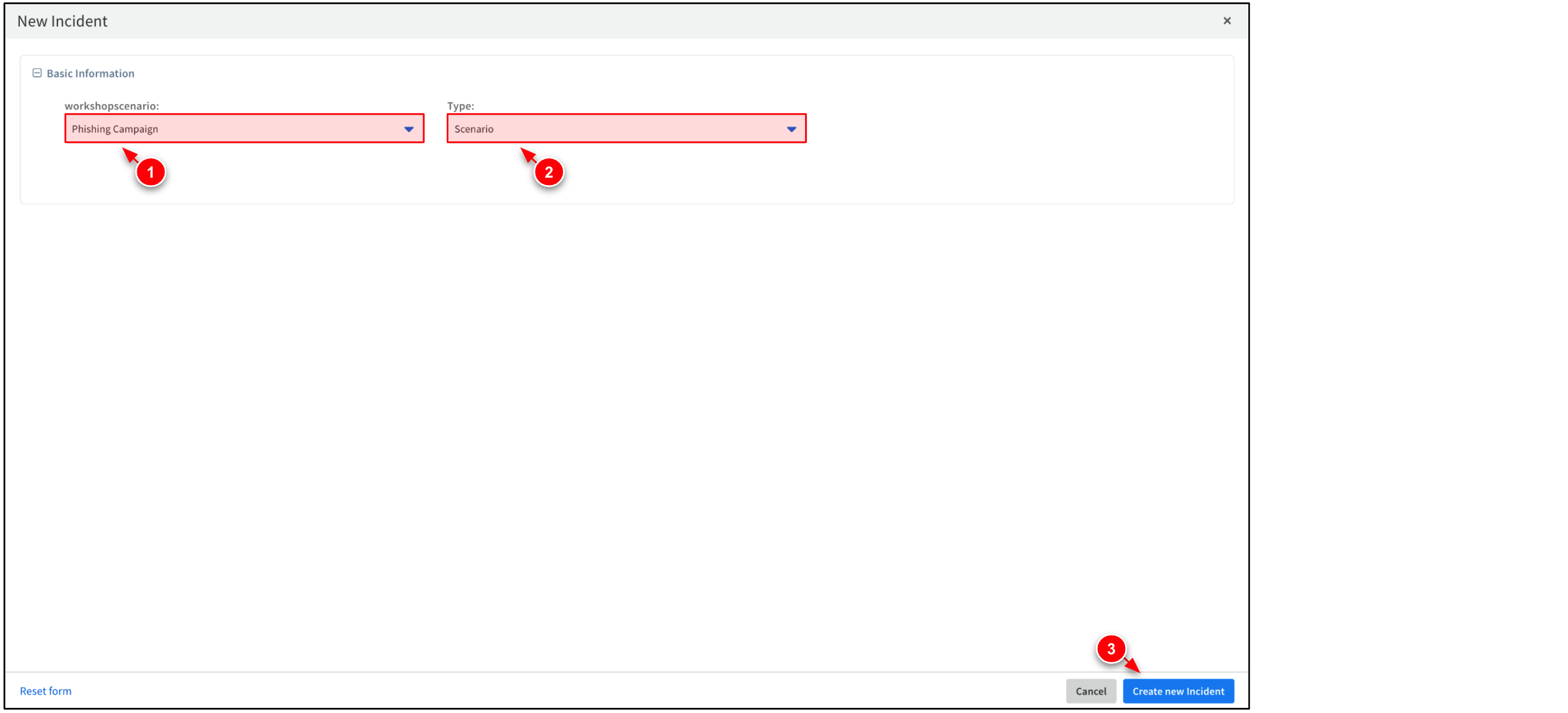
Set the workshopscenario to Phishing Campaign and Type to Scenario. Then, click Create New Incident.
While waiting for the incident to generate, open any existing incident to view more information about it.
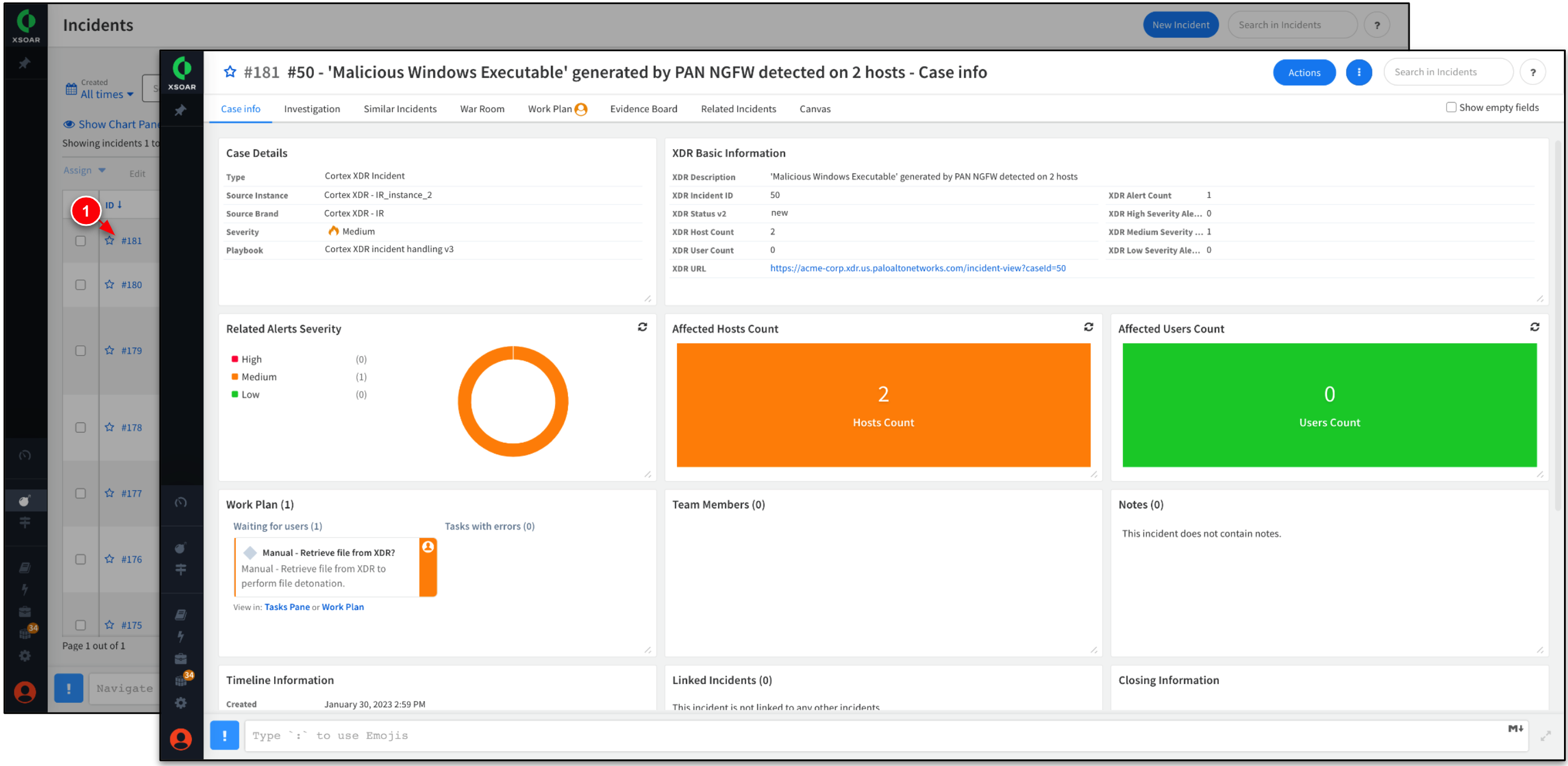
In this step, investigate the phishing incident that was created in the previous step, including the incident's timeline, status, and associated evidence.
While within Incidents, enter the search below to filter for incidents that use the Email Phishing playbook.
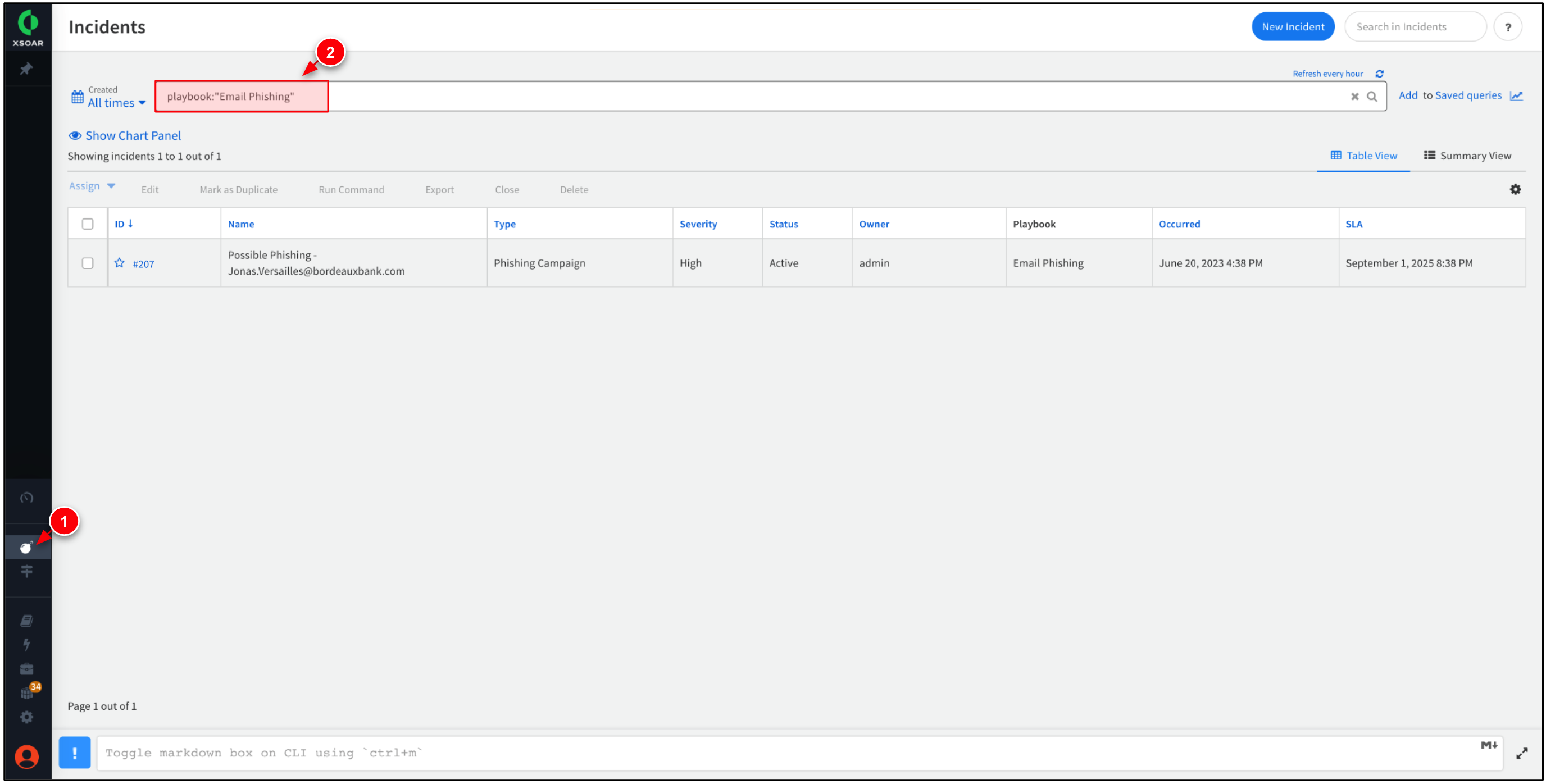
Select the most recent incident to view more information about it.
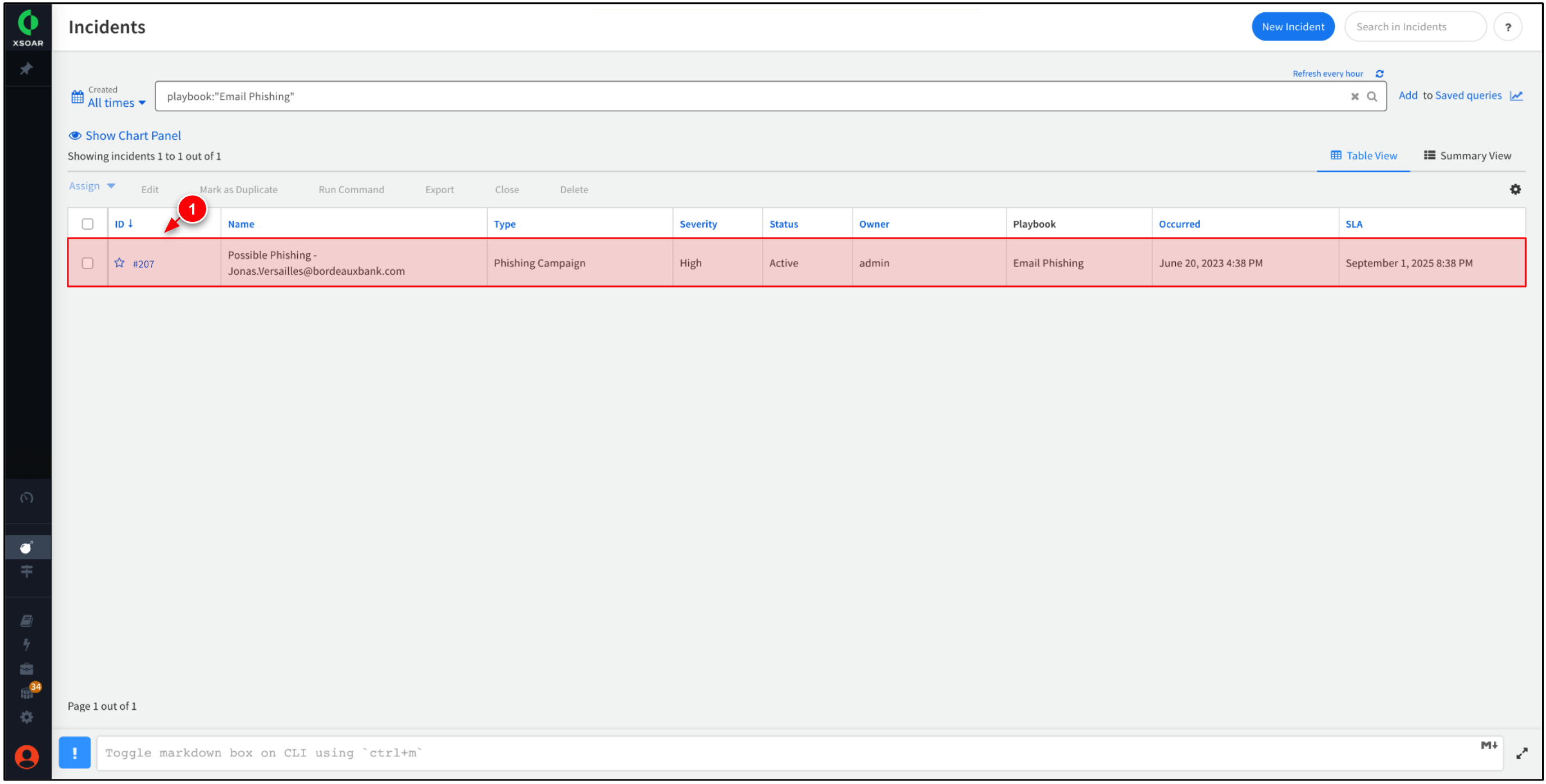
Active. This is because the Work Plan associated with this incident type has not been completed, or is waiting for manual intervention.
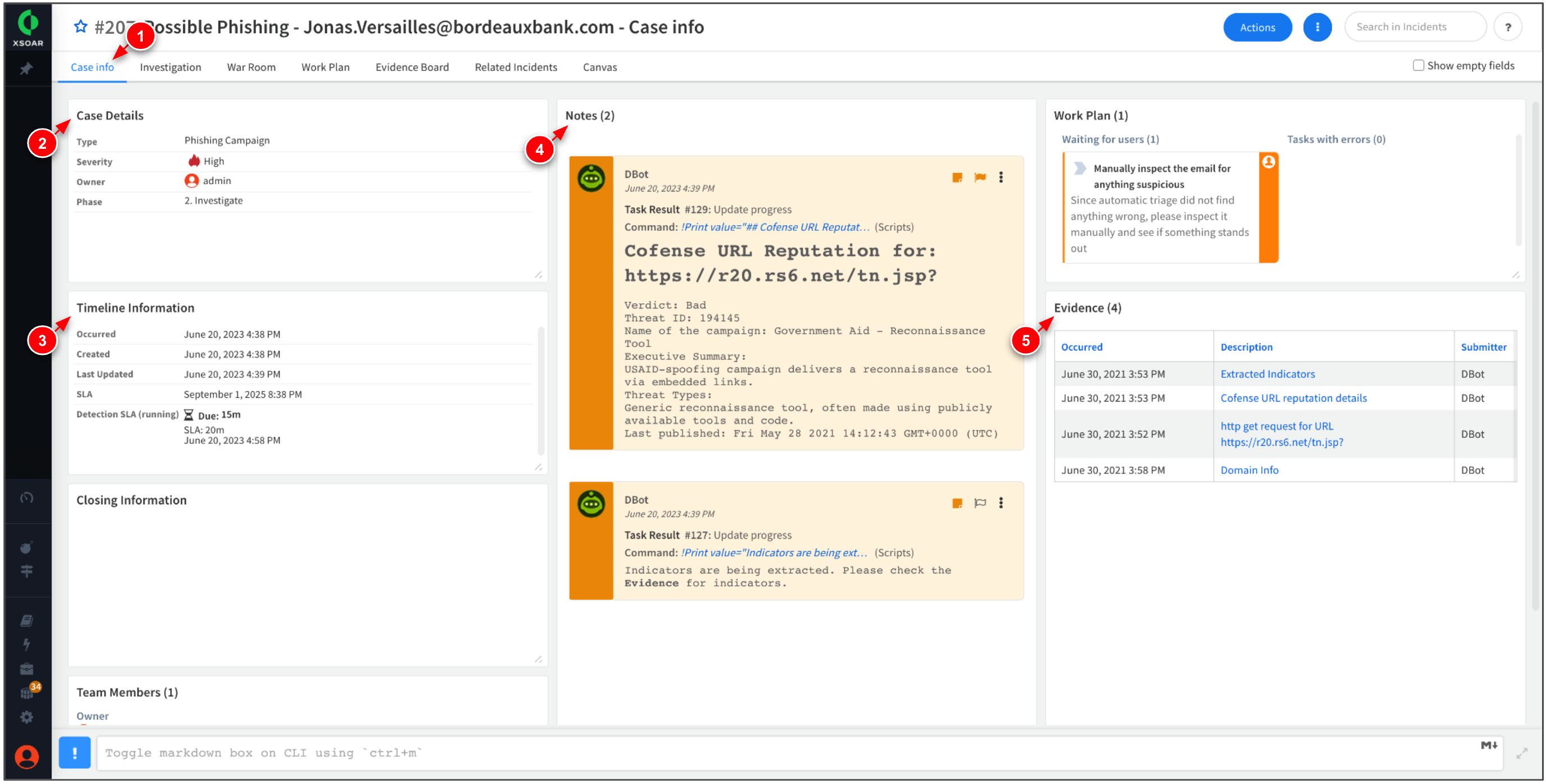
Click Case Info tab. Take time to review the case details, timeline, notes, and evidence.
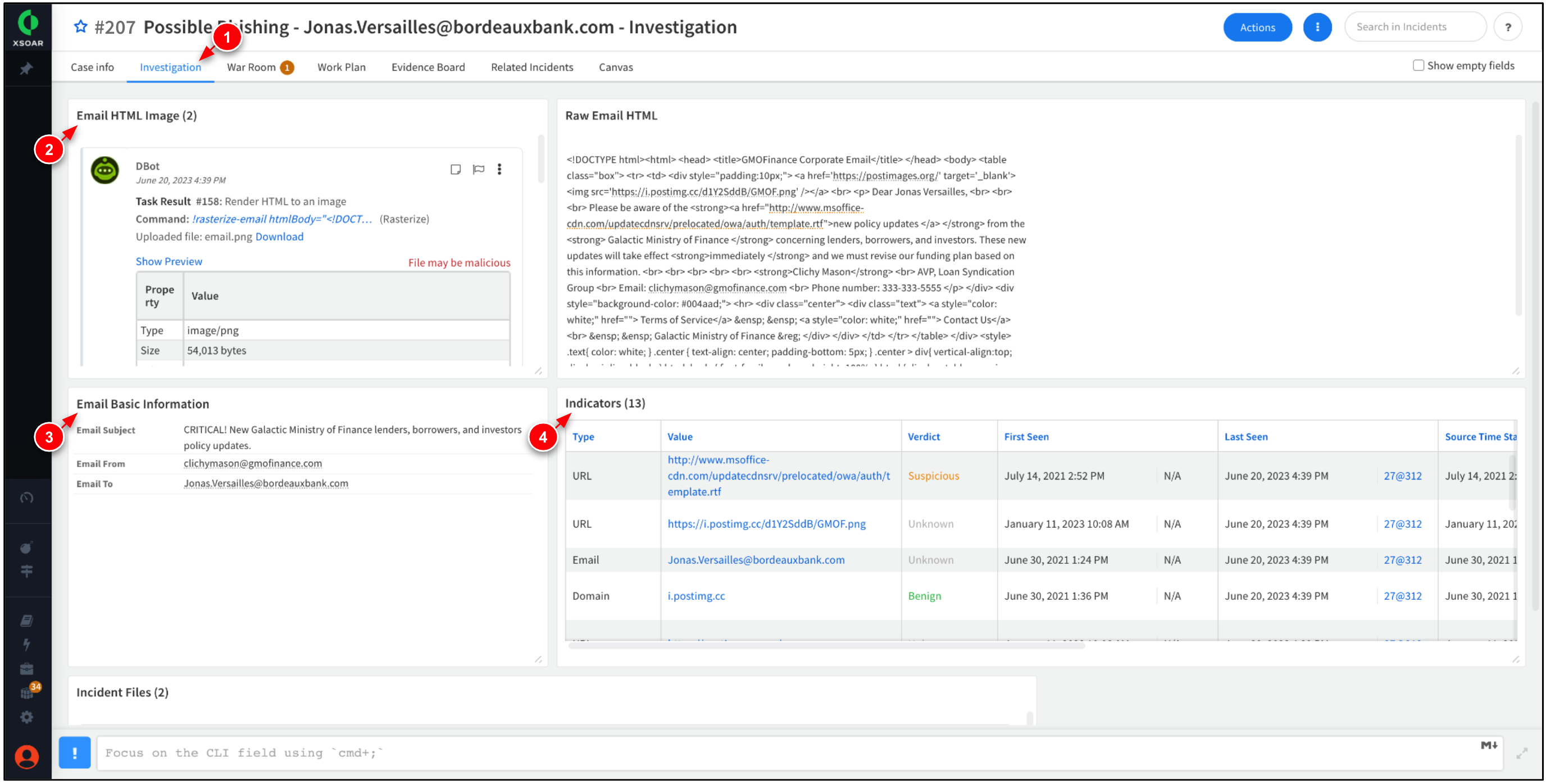
Click the Investigation tab. Review the contents of the e-mail, including any associated indicators, and incident files.
In this task, work within XSOAR War Rooms and Work Plans to understand and remediate phishing incidents.
A War Room centralized workspace that facilitates collaboration, incident response, and threat intelligence among security teams. In this step, navigate to the incident's War Room to view a consolidated pane of all the events related to the phishing incident.
The War Room tab has a notification icon, indicating manual intervention is required for this particular incident. Click the War Room tab.
Take time to scroll through the events associated with the incident.
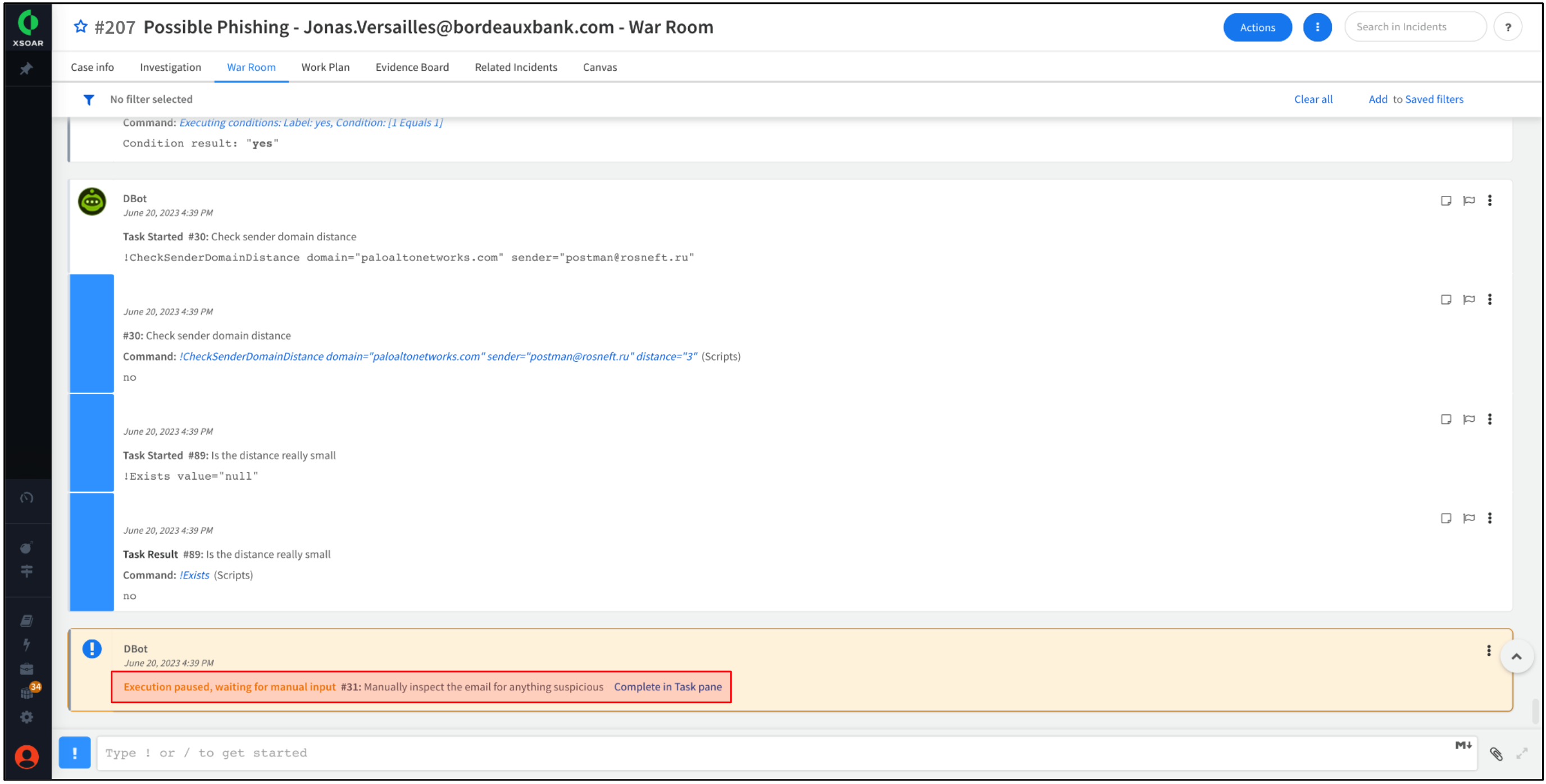
At the bottom, a message states the execution of the Work Plan has been paused.
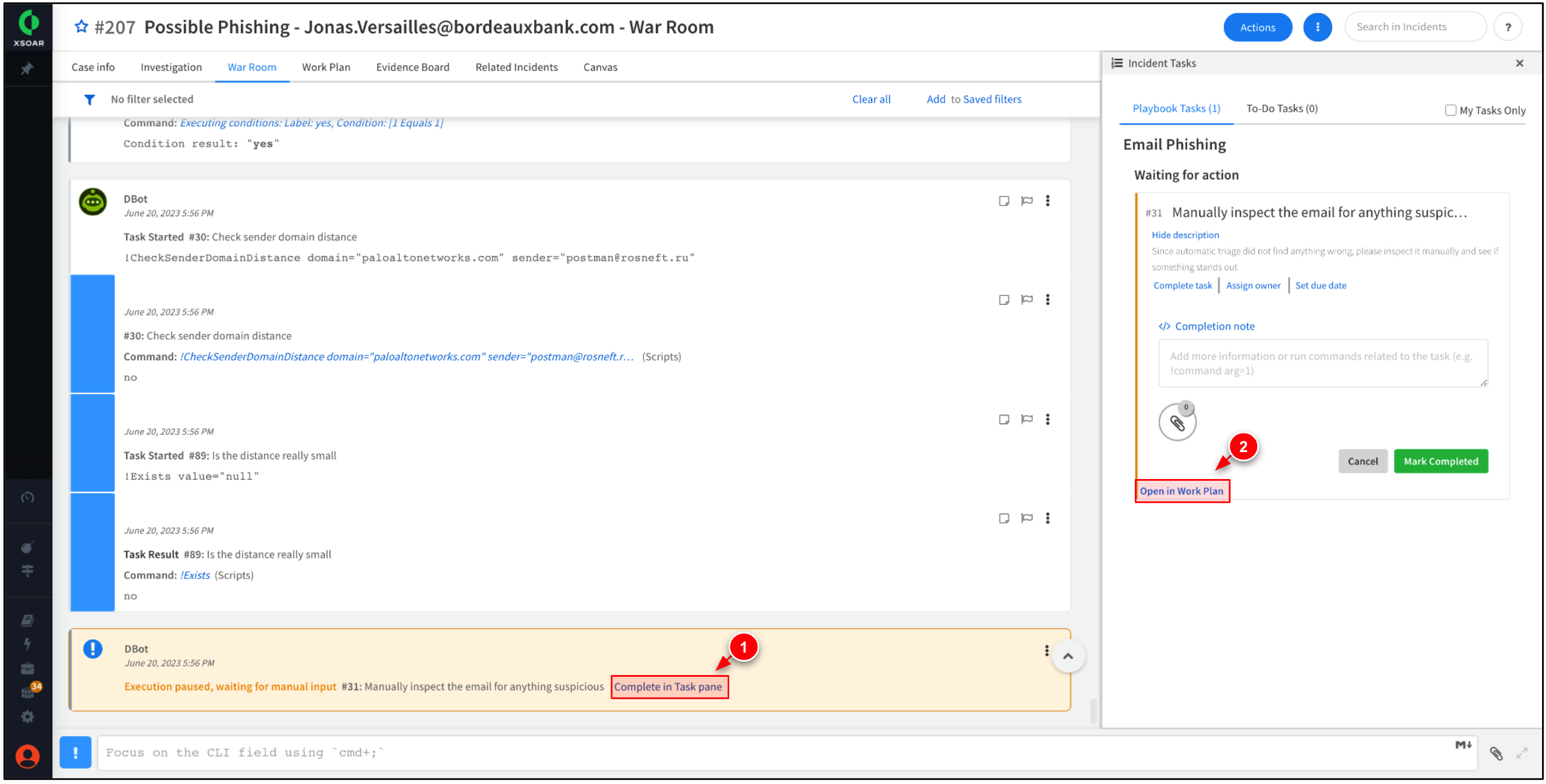
Click Complete in Task pane → Open in Work Plan.
In this step, navigate to the incident's Work Plan to view the steps and actions taken to respond to the phishing incident. The Work Plan provides a visual representation of the steps and actions to be taken when responding to specific security incidents or events.
The previous step brings you to a incomplete task within the Work Plan tab. The tasks is requesting manual investigation into the email.
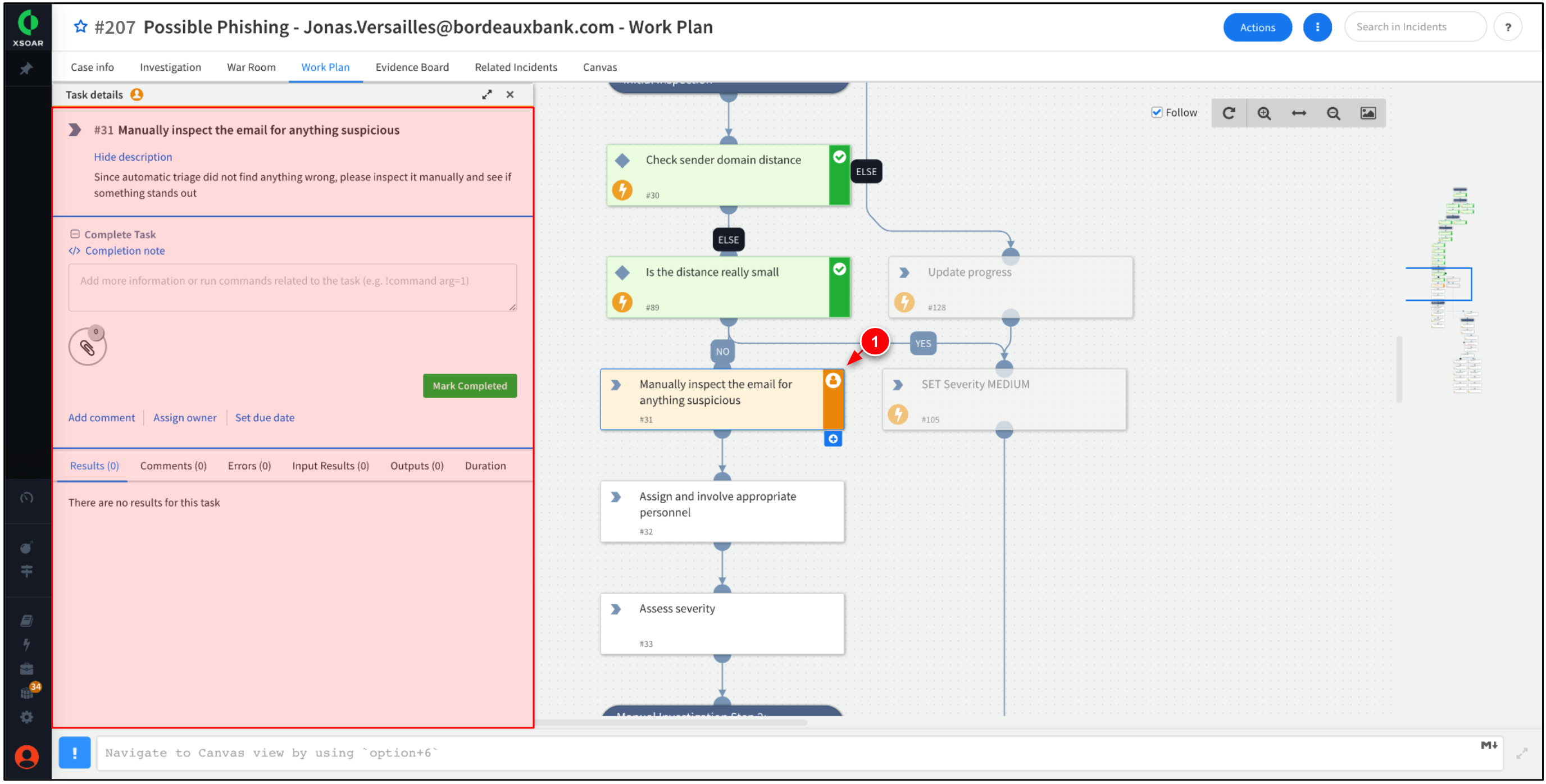
Since we already have investigated the email, click Mark Completed.
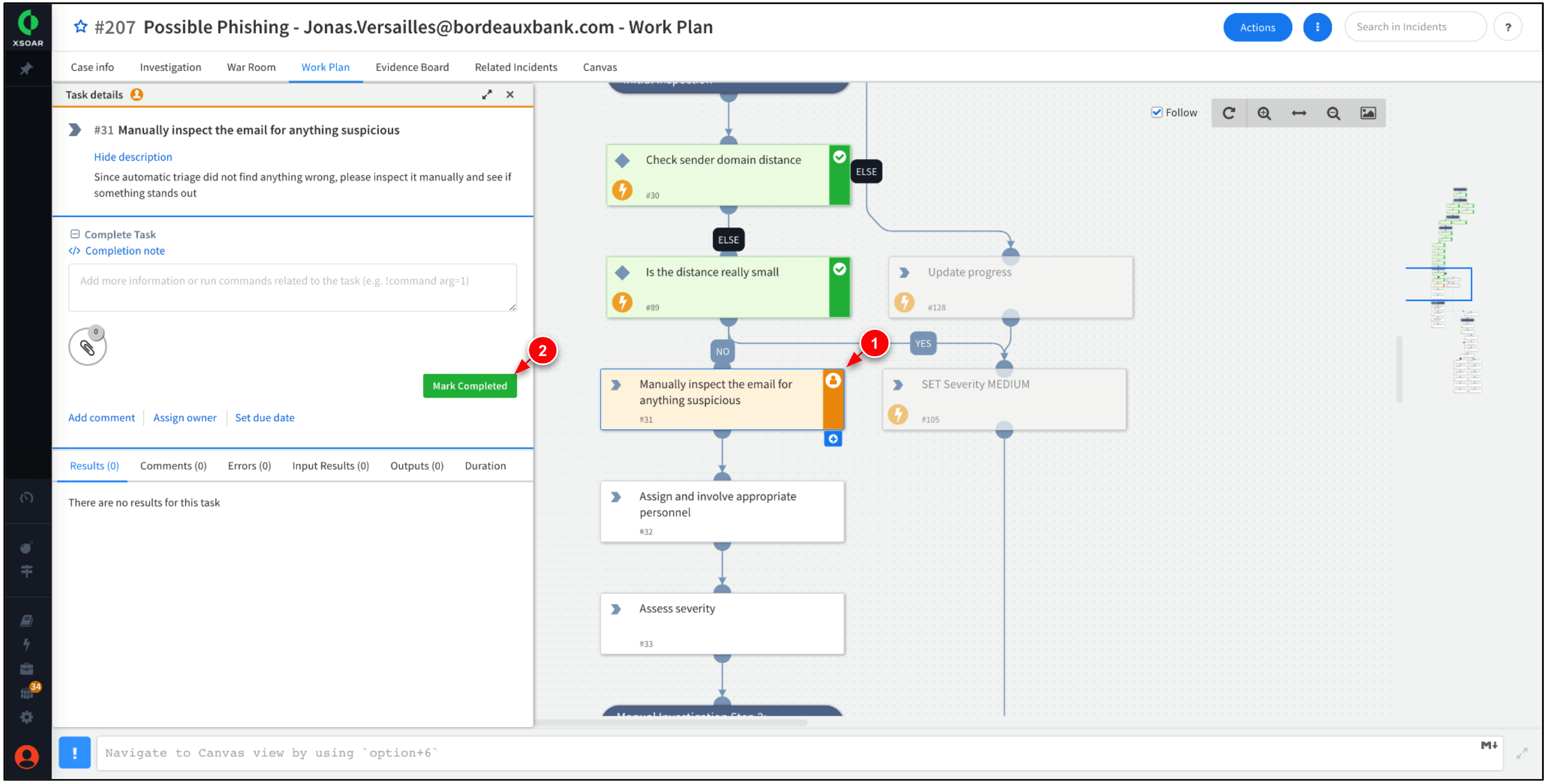
The Work Plan should progress the task, Assign and involve appropriate personnel. Click Mark Completed.
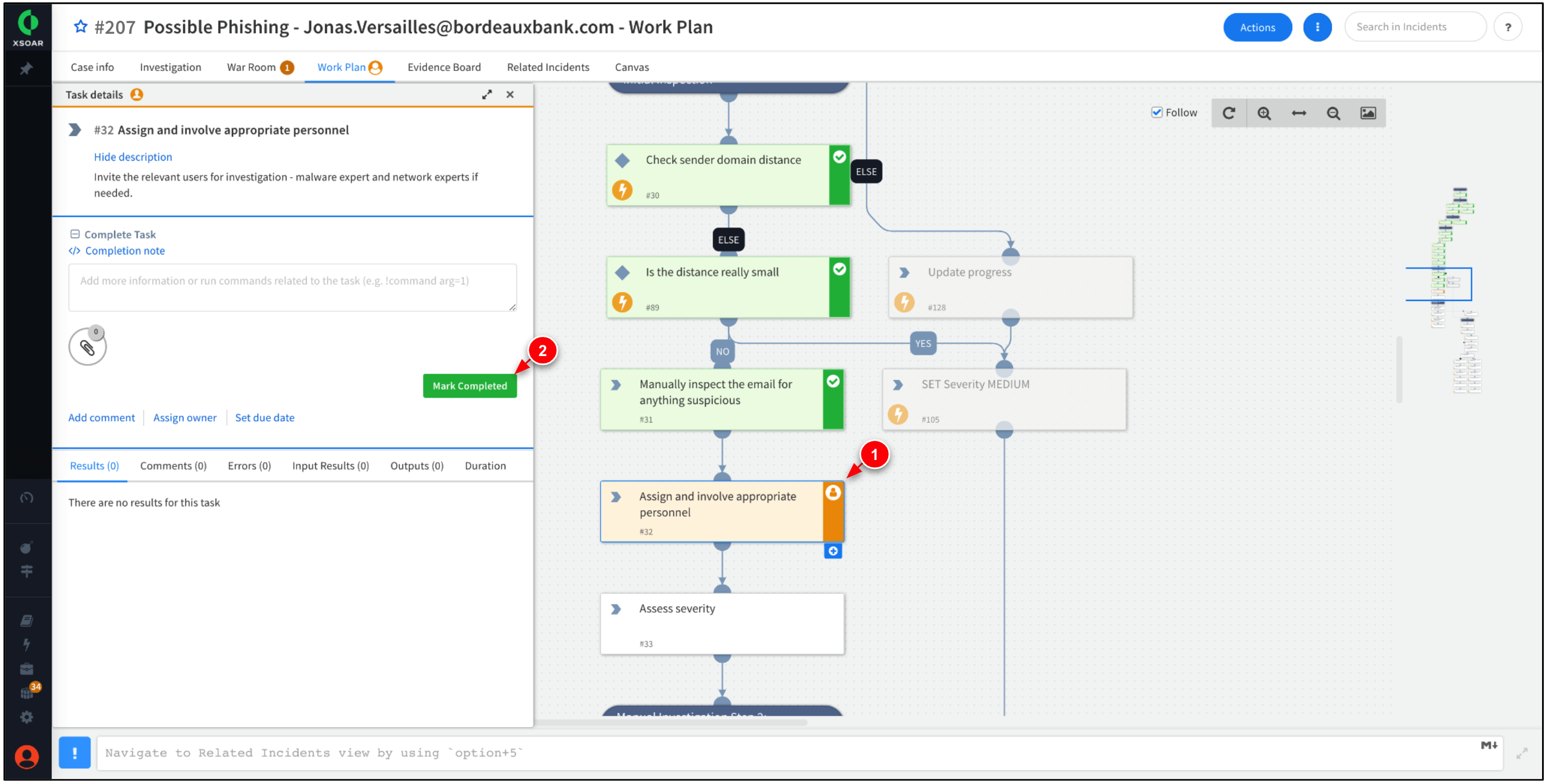
The Work Plan should progress the task, Assess severity. Click Mark Completed.
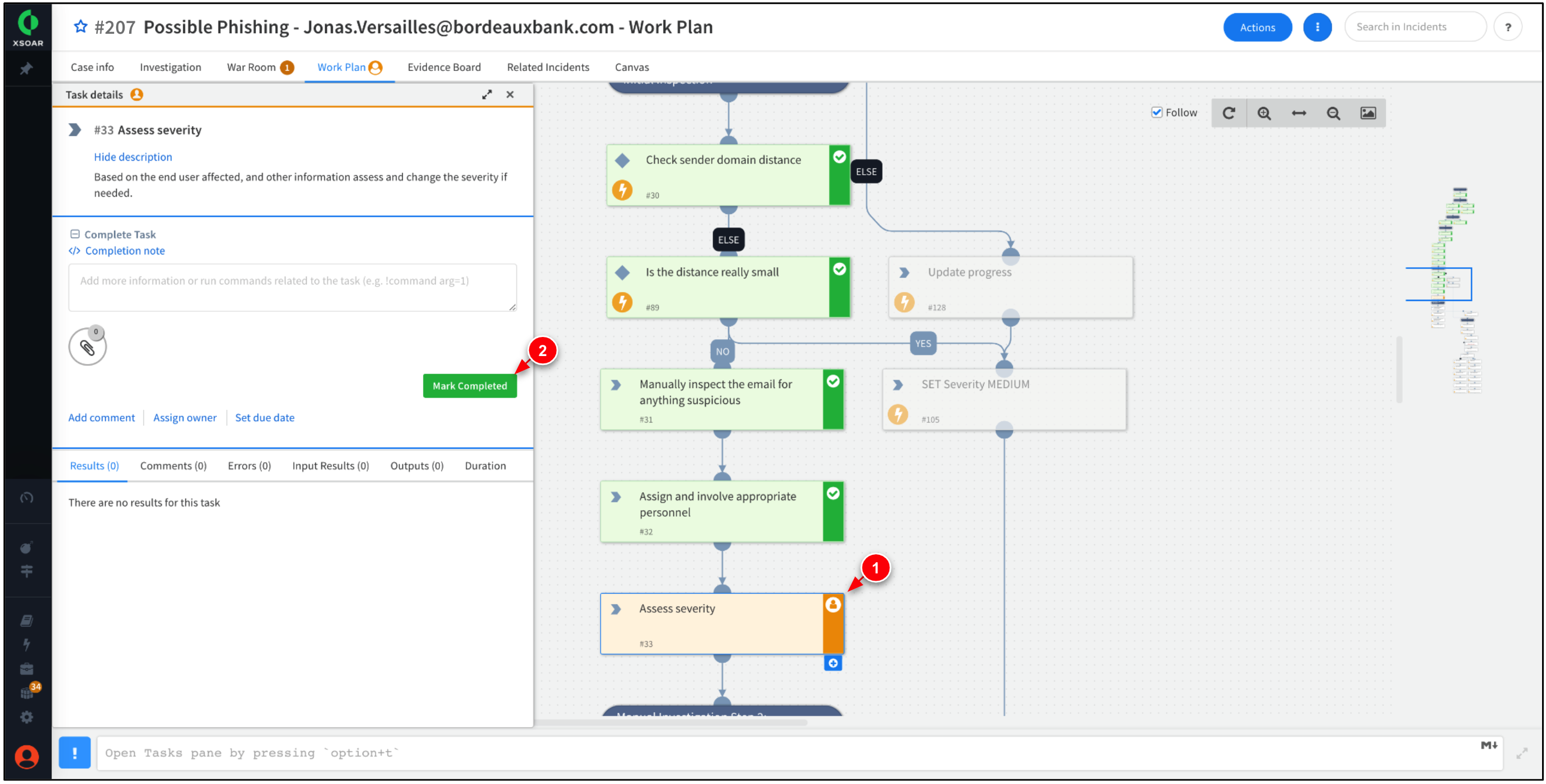
The Work Plan should progress the task, Are the hostnames in the urls being misrepresented? Click Mark Completed.
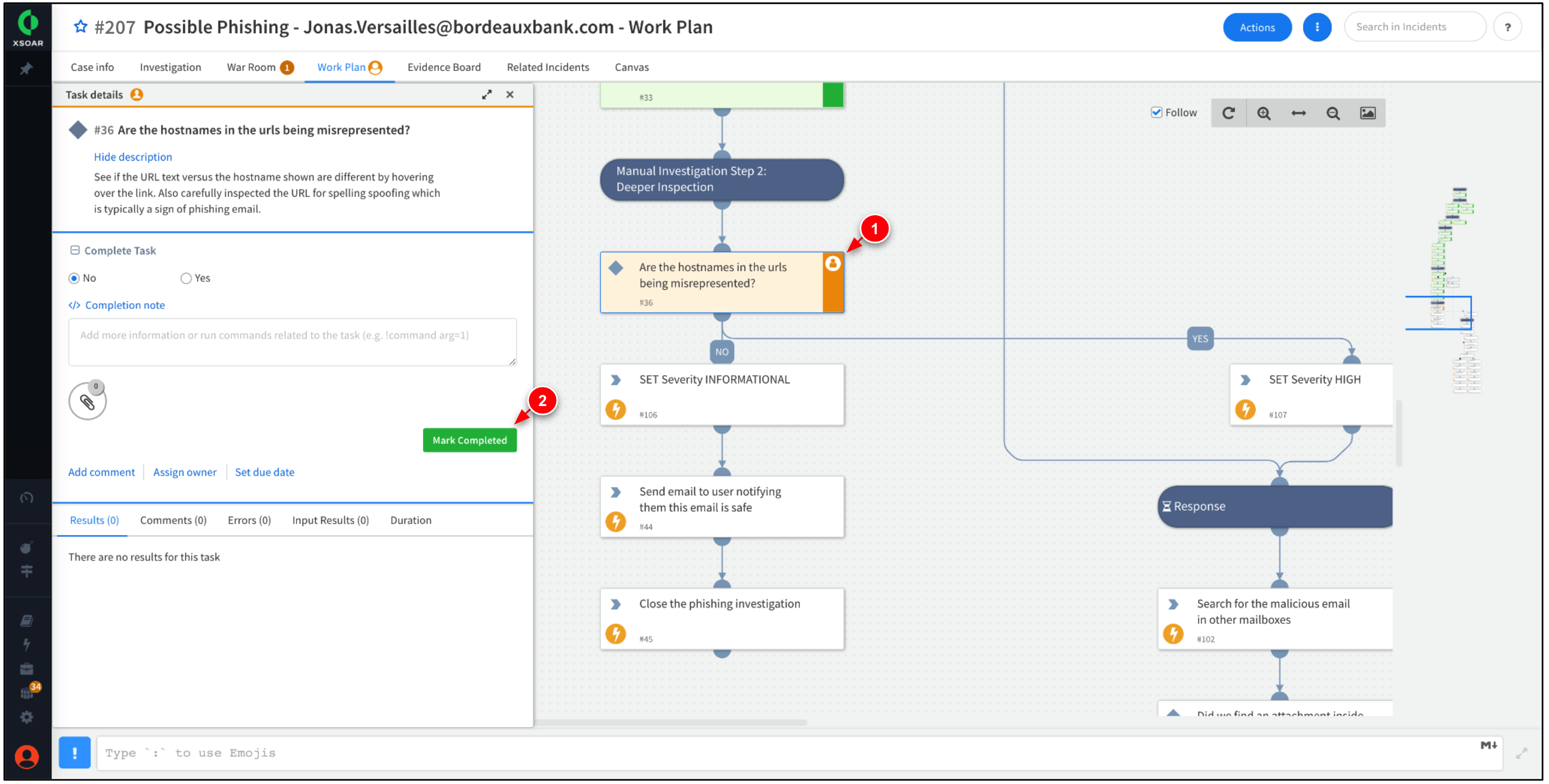
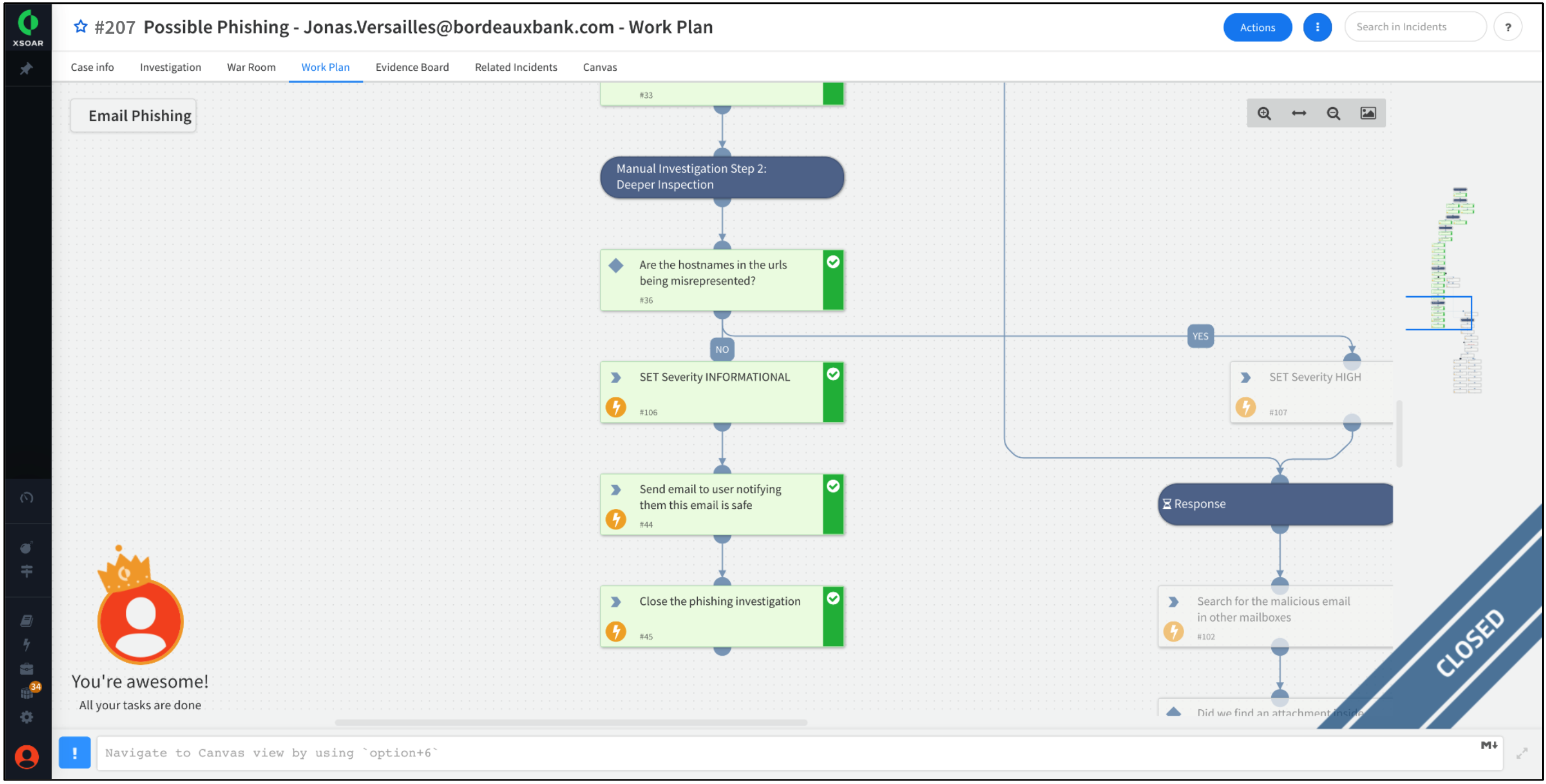
The Work Plan should now be marked as completed. Feel free to explore any of the tasks in the Work Plan for additional information and insights.
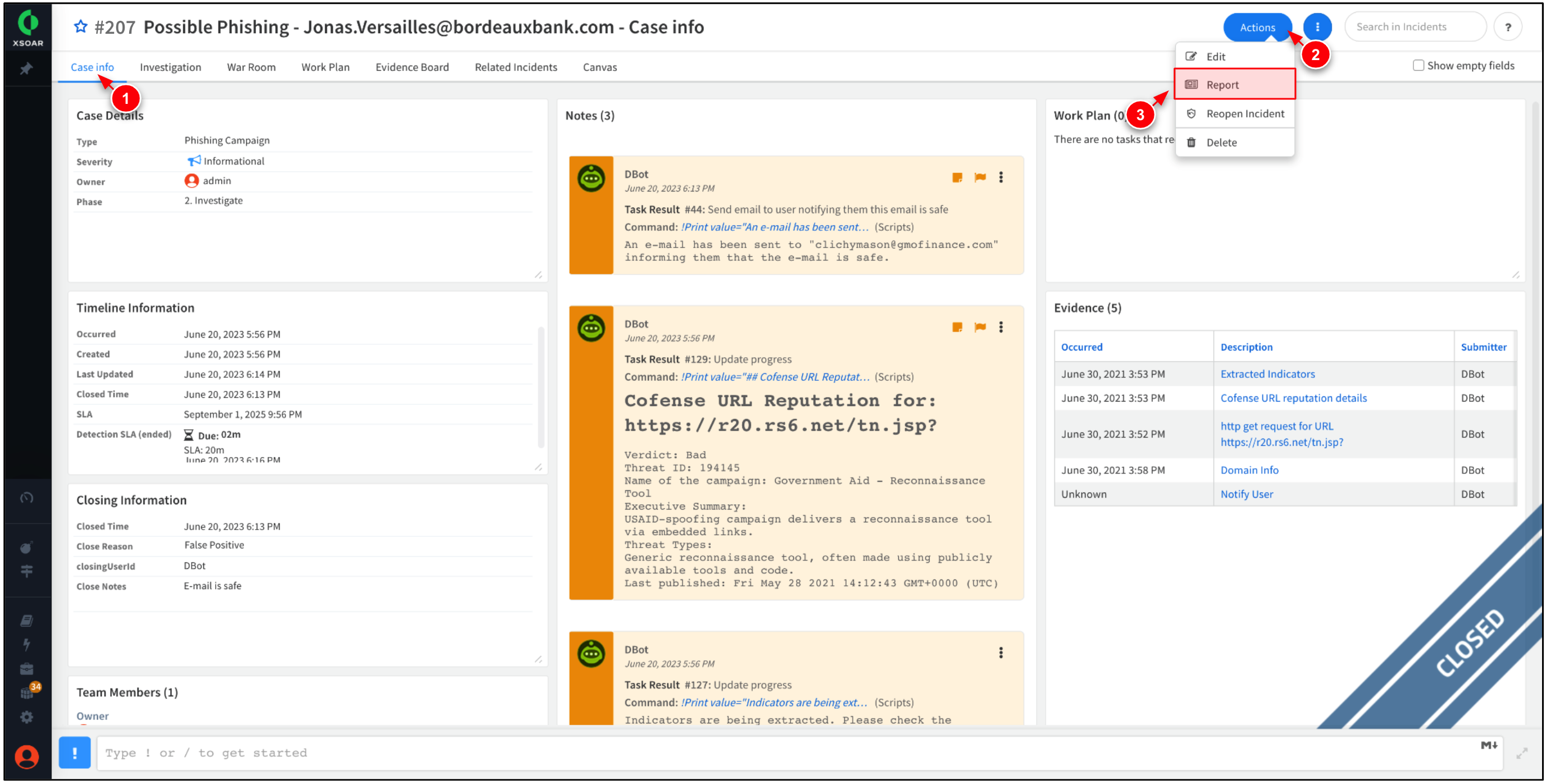
XSOAR offers extensive reporting capabilities out of the box, including pre-built reports and dashboards, it also allows you to create custom reports to suit your specific needs. In this step, create a report about the phishing incident.
While within the Incident, go to Case Info → Actions → Report.
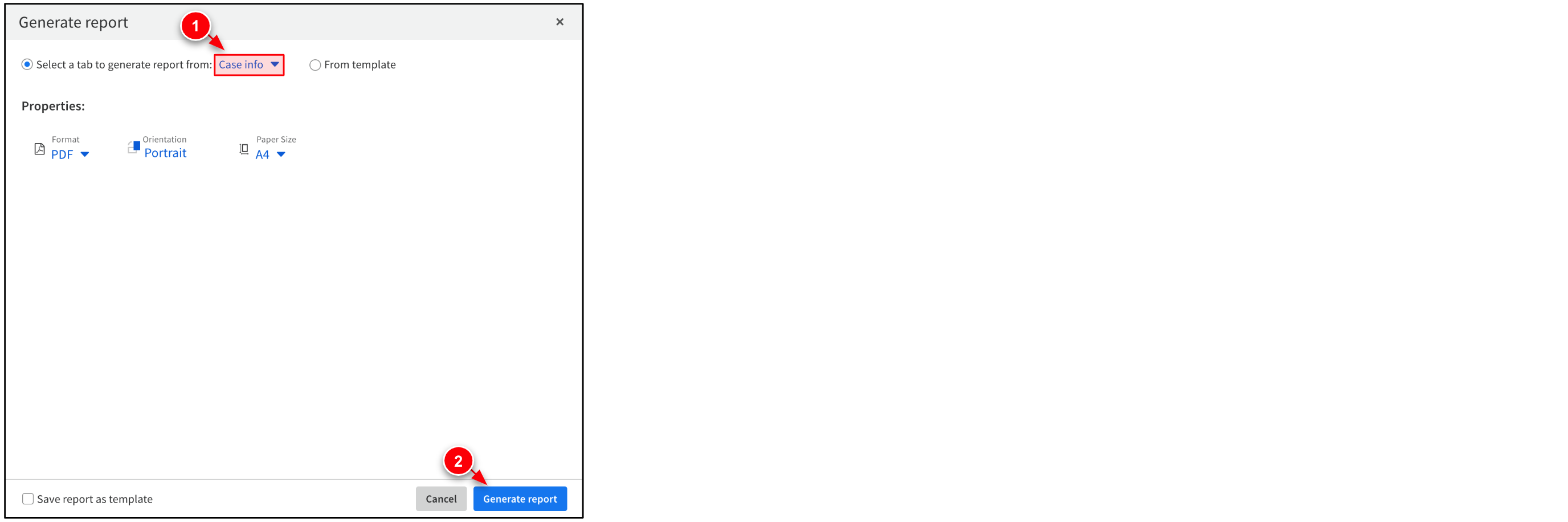
Set Select a tab to generate report from to Case info. Then, click Generate report.
Hover over the XSOAR logo on the top left, and click on Dashboards & Reports. Click the Reports tab to download the report to your machine.

In this lab you learned to use Cortex XSOAR to respond to phishing incidents. You also learned how to generate reports, navigate War Room, and complete Work Plans and playbooks.
To learn more, check out the following resources:




Ta treść jest obecnie niedostępna
Kiedy dostępność się zmieni, wyślemy Ci e-maila z powiadomieniem

Świetnie
Kiedy dostępność się zmieni, skontaktujemy się z Tobą e-mailem


One lab at a time
Confirm to end all existing labs and start this one
