Checkpoints
Enable Gemini
/ 35
Create a GKE cluster and deploy a web app
/ 35
Remediate a security misconfiguration
/ 30
Navigate Security Decisions with Gemini
Overview
Gemini for Google Cloud is an always-on AI collaborator that provides help to users of all skill levels where they need it. In this lab, you will learn how to identify and remediate security misconfigurations in your Google Cloud environment using Security Command Center's Gemini features.
Objectives
In this lab, you will learn how to perform the following tasks:
- Enable Gemini in a Google Cloud project
- Deploy example workloads into an environment in Google Cloud
- Identify security misconfigurations with Gemini
- Remediate security misconfigurations with Gemini
Scenario
As you monitor your infrastructure for ways to improve your security posture, Gemini can help identify infrastructure or configuration changes that will prevent issues in the future.
In this example, consider that you are a security engineer at an ecommerce company where managed Kubernetes clusters are regularly deployed. You need a way to see if there are any misconfigurations, and you want quick instructions to help fix those issues in your cloud environment.
Setup and requirements
For each lab, you get a new Google Cloud project and set of resources for a fixed time at no cost.
-
Sign in to Qwiklabs using an incognito window.
-
Note the lab's access time (for example,
1:15:00), and make sure you can finish within that time.
There is no pause feature. You can restart if needed, but you have to start at the beginning. -
When ready, click Start lab.
-
Note your lab credentials (Username and Password). You will use them to sign in to the Google Cloud Console.
-
Click Open Google Console.
-
Click Use another account and copy/paste credentials for this lab into the prompts.
If you use other credentials, you'll receive errors or incur charges. -
Accept the terms and skip the recovery resource page.
Task 1. Enable Gemini
You will first enable Gemini in your Google Cloud project and configure the necessary permissions for your Google Cloud Qwiklabs user account.
-
Click on the Cloud Shell icon (
) in the top-right corner of the Google Cloud console toolbar.
-
To set your project ID and region environment variables, run the following commands:
- To store the signed-in Google user account in an environment variable, run the following command:
-
Click Authorize if prompted.
-
Enable the Cloud AI Companion API for Gemini:
- To use Gemini, grant the necessary IAM roles to your Google Cloud Qwiklabs user account:
Adding these roles lets the user use Gemini assistance.
Click Check my progress to verify your performed task.
Task 2. Create a GKE cluster and deploy a web app
You will now be creating a Google Kubernetes Engine (GKE) cluster running a handful of microservices.
- Run the following command to create a GKE cluster named
test:
This should take a few minutes. Upon completion, you should see a result similar to the following:
- Now, clone a repository that contains code for a web app:
- Use kubectl to deploy a set of microservices to the GKE cluster:
- After a couple minutes, run the following command to get the public IP address to access your web app in a browser:
- Copy the IP address from the output of the above command and paste it into a new browser tab.
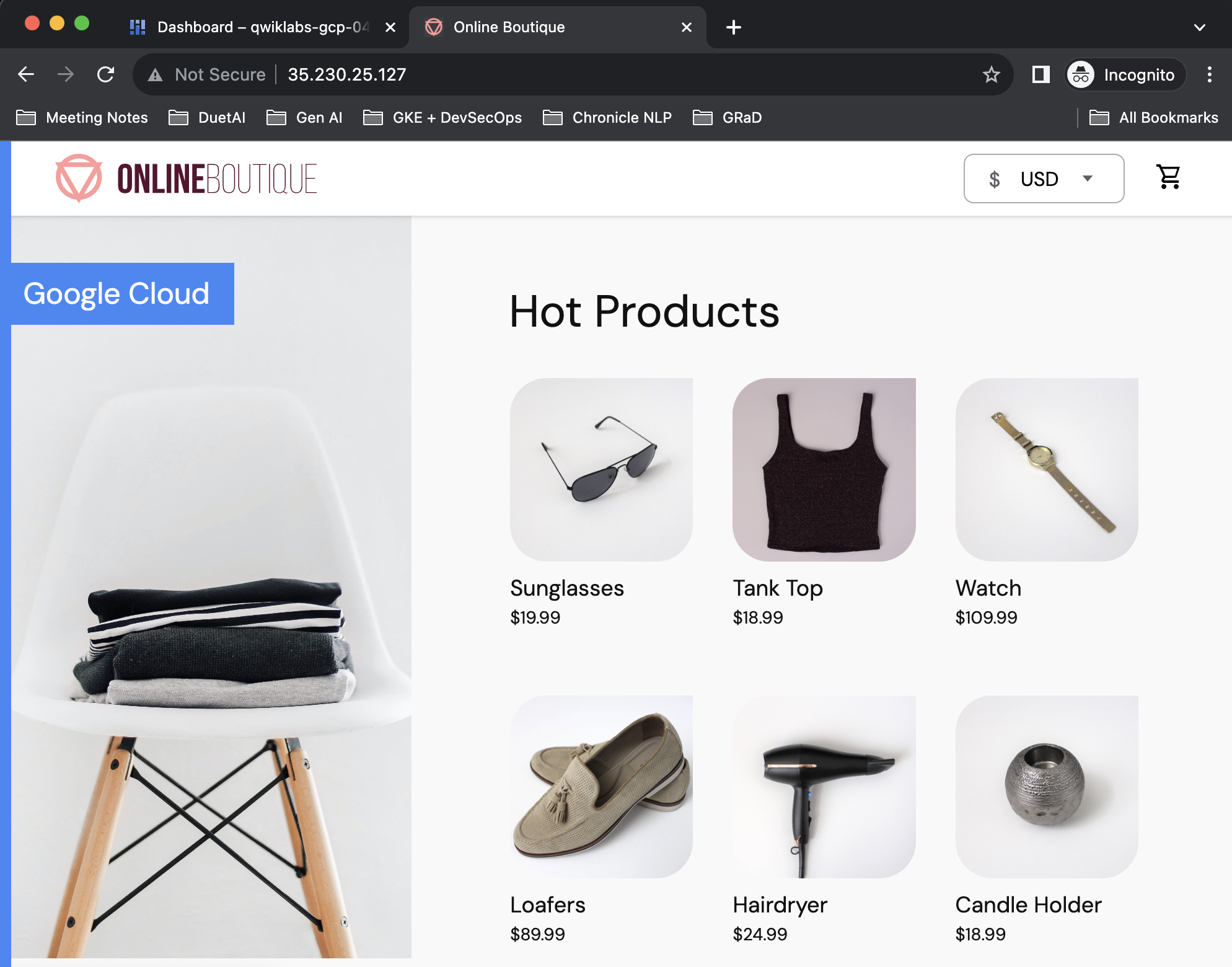
You should see a web app similar to the following:
Click Check my progress to verify your performed task.
Task 3. Identify security misconfigurations with Gemini
Now that you have an existing GKE cluster running an ecommerce app, you will identify areas where you can improve your security posture with Gemini.
-
Return to your tab with the Google Cloud console.
-
Refresh the Google Cloud console page.
-
Minimize the Cloud Shell pane.
-
Click on the Gemini icon (
) in the top-right corner of the Google Cloud console toolbar.
-
Click Start Chatting.
-
Enter the following prompt:
Gemini should respond with something similar to the following:
- Security Command Center can help you identify and prioritize security risks across your Google Cloud environment, including GKE clusters.
- Cloud Asset Inventory can help you track and manage your Google Cloud resources, including GKE clusters.
- Cloud Logging can help you collect and analyze logs from your GKE clusters.
- Cloud Monitoring can help you monitor the performance and health of your GKE clusters.
In this scenario, you decide that Security Command Center sounds like the right place to start.
- Open the Navigation menu and select Security > Risk Overview.
With multiple visualizations discussing vulnerabilities, you want to ask Gemini to help you quickly understand what is classified as a vulnerability in Security Command Center.
- Enter the following prompt:
Gemini's response should be similar to the following:
Source: https://cloud.google.com/security-command-center/docs/finding-classes
-
Click on the documentation link to better disambiguate between finding classes.
-
After reading about them, close the tab and return to the Google Cloud console.
-
Click Findings from the sidebar of the Google Cloud console.
-
To see the findings for your GKE cluster, find the "Quick Filters" section and select Google container cluster under Resource Type.
You should see a number of Medium severity findings.
- Click on the Cluster secrets encryption disabled finding.
At the top of this finding panel, you should see a section titled "Description" with a summary similar to the following:
-
Exit out of this information panel.
-
Next, click on the Over privileged account finding and view the summary in the description which is similar to the following:
-
Exit out of this information panel.
-
Finally, click on the Master authorized networks disabled finding. You should see a description similar to the following:
- Exit out of this information panel.
Now that you have an understanding of some of your environment's security misconfigurations, you will leverage Gemini's recommendations to remediate them.
Task 4. Remediate a security misconfiguration
Now that you have had the opportunity to review multiple areas to begin improving the security of your GKE cluster, you will remediate the "Master authorized networks disabled" finding using the instructions provided by Gemini's summary in Security Command Center.
-
Open the Navigation menu and select Kubernetes Engine > Clusters.
-
Click the name of the cluster you created earlier ("test").
-
Scroll down to the Networking section.
-
Click on the pencil icon next to Control plane authorized networks.
-
Check the box next to Enable control plane authorized networks.
-
Check the box underneath Allow access through Google Cloud public IP addresses.
-
Click Save changes.
-
Click Clusters in the sidebar.
You will see cluster being updated, shown by a spinning wheel or half green circle icon in the Status section.
-
While the network policy updates for the control plane take place, open Gemini from the Google Cloud console toolbar.
-
Enter the following prompt:
Gemini's response should be similar to the following:
To add an authorized network, go to the Google Kubernetes Engine page in the Google Cloud console. Click the name of the cluster you want to modify. Under Networking, in the Control plane authorized networks field, click edit Edit control plane authorized networks...
Applying the updated control plane policy may take a few minutes to take effect.
- Once you see a green checkmark in the Status column next to your cluster, you have successfully updated your cluster configuration.
Click Check my progress to verify your performed task.
End your lab
When you have completed your lab, click End Lab. Qwiklabs removes the resources you’ve used and cleans the account for you.
You will be given an opportunity to rate the lab experience. Select the applicable number of stars, type a comment, and then click Submit.
The number of stars indicates the following:
- 1 star = Very dissatisfied
- 2 stars = Dissatisfied
- 3 stars = Neutral
- 4 stars = Satisfied
- 5 stars = Very satisfied
You can close the dialog box if you don't want to provide feedback.
For feedback, suggestions, or corrections, please use the Support tab.
Copyright 2024 Google LLC All rights reserved. Google and the Google logo are trademarks of Google LLC. All other company and product names may be trademarks of the respective companies with which they are associated.